BYOD shortcomings

BYOD (Bring Your Own Device) is not secure. Every Enterprise Mobility Security consultants will claim not to use BYOD
They are right.
They advise to choose expansive Mobile Device Management as COPE. Sometimes they belong also to MDM solution vendors. Most of these MDM solutions are
- expensive and
- only apply for your employees not for your external person
Main BYOD shortcomings are
You can’t control their choice or the model they want.
- not everyone will be utilizing the same type of devices. Some may prefer Androids other Apple
- user install any program or games he wants,
- even root or jailbreak their device (<2%)
If your EMM impose a control on employees’devices, obviously you can’t control your external stakeholders (client, supplier, partners): they choose the devices and install the mobile apps they prefer.
In a COPE strategy your employee accept to use 2 devices? with the burden of
- wearing 2 devices
- mix the contact list
- having 2 separate calendars, lists of contact, not so easy
When data resides in the mobile device
- Who is really in front of the device?
- Other application installed in the device might have access
- Malicious app can reside in the device, device is subject to phishing attempts
- Automatic synchronization of data in a “free” cloud. Your sensitive data might be synchronized ?
- Does this cloud belong to an enterprise whose business model is based on data commercialization?
- Where is located the cloud? If in the US or affiliate countries: Patriot Act, SafeHarbor or Cloud acts apply
- the device might jailbreak or rooted
- Is the device in a safe place or in a risky location
- Security of the internet transfer especially in public WIFI (restaurants, coffee shops, gym, railway, internet cafe…)
- Man in the Middle risk (4%)
- Malware infextion,
- Public internet connection conditions of use (the easy to press “accept all” button)
the user and all the errors in using the device
- who is really in front of the device?
- let the the device unattended, forget it or even losing it (and worse stolen)
- lending it to the kids to play
- sharing the family PC at home
- giving or selling the device to other without deleting its contents
- leaving the organization

A Digital Safe embarked in your device
To overcome BYOD shortcomings, ChatCal architects follows the “Privacy by Design” principles that led to a embark a digital safe in your device.
When you install ChatCal in your device, the installation creates automatically a safe container in your device.
This safe protect the ChatCal app and its information database from the app and malware of the device
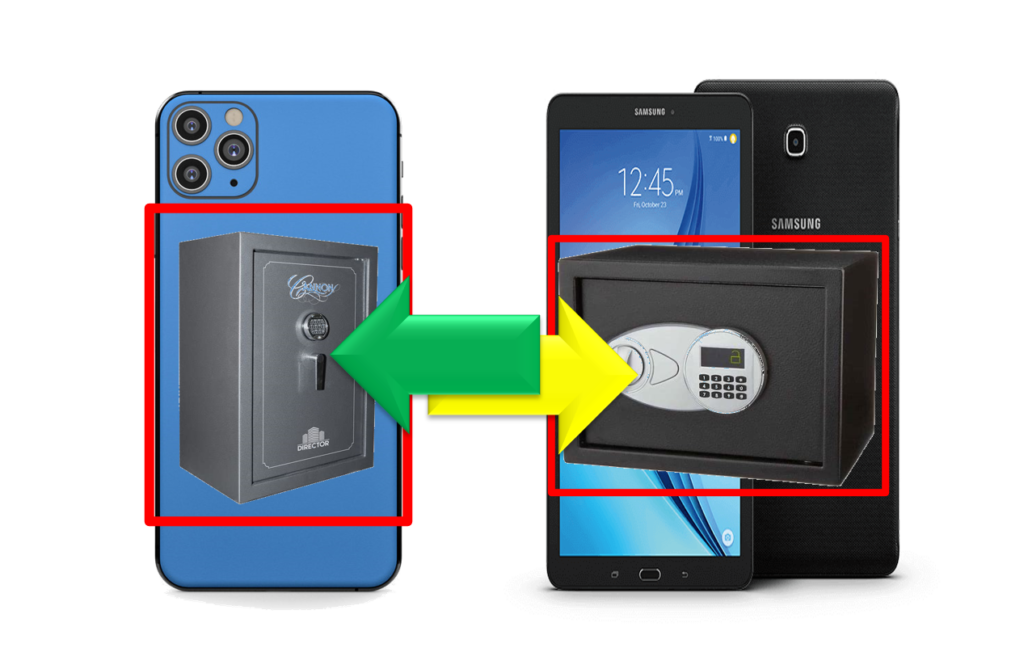
A “safe to safe” communication
Using ChatCal, you communicate “Safe to Safe”
- Your data are in the safe of your correspondants
- Their data are in your safe
This “safe to safe” communication ensures the automatic mutual protection of the information. When your information gets mobile in other’s device, it’s protected.
and for more privacy, this safe is desined using a Citrus architecture.
Citrus architecture


Information is the juice of your company
Your business information is a flow of information that irrigate your organization and its collaborators and external stakeholders (clients, suppliers, partners) and even the public. A fast, safe and private information flow increases your vitality
Just imagine that this flow of information is a citrus juice.
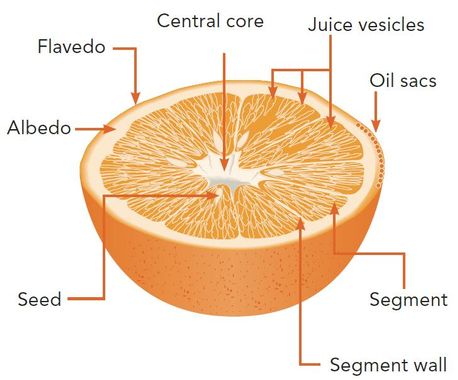
Overview
ChatCal propose to share this juice safely and securely within your stakeholders in a collaborative manner.
This information is composed of
- Event metadata
- its participants, their role, their participating devices
- their documents, multimedia contributions,
- their comments,
- their opinions: votes, rating and like



Event is the juice pulp
An event is the pulp containing the juice: your information
Events are the various communication as: message, chat, discussion, meeting, seminar, tasks, travel…
Each pulp juice is protected with a tiny skin: the vesicle. Similarly the event protects its content in a sealed envelope that is only accessible to the participant of this event.

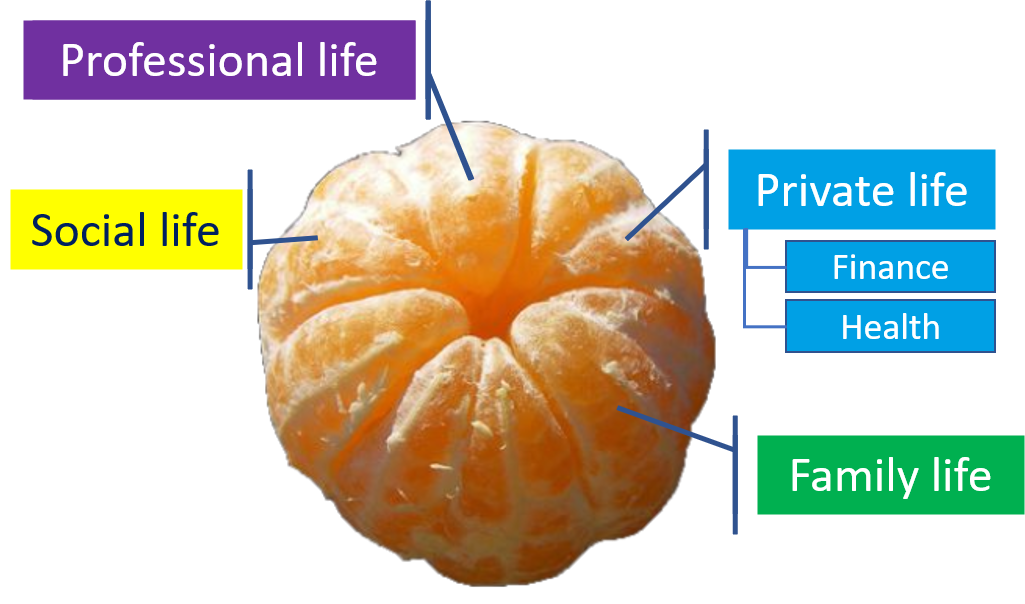
Segment as life
As a person, your life is segmented in:
- professional life,
- private life,
- Health
- Finance
- familial life,
- social life (sport, association, club, charity…
As the segments gather the juice pulps, events and their information are segregated between your different lives, protecting privacy of each life
As segments are protected by walls, each life can be compared to a safe containing sealed envelopes (events) thus
- protecting information privacy of your life segments
- sharing calendars with business colleagues in hiding private life protects your personal privacy





Peel as a container
The peel (Albodo and Flavodo) protect the citrus against external threats as a container protects ChatCal and its content against:
- Virus and malware
- Other apps installed in the device, no app can access an event
- Import a agenda is authorized for a user. This newly created event is in the sealed envelop. The user can fill some complementary element as the life, reminders… This event will be synchronized only among his devices, unless the user wants to invite people and share information.
- Export of the event information is reserved to event’s administrator role and is traced in BlueSafe server for audit purpose (and help Security Officer to catch red handed)
