Main features

BlueChatCal is a new disruptive communication solution combining
a chat, a calendar and a Record Management
Companies projects and business processes as well as our life are made of events
Manage event that

is something that happens over a certain period of time
From few seconds to many days during an “active period” until its archiving
This event
- is of multiple type: from a simple message, a discussion, a meeting, a seminar, a task, a reminder and many other…
- gathers persons around a subject
- only you as in an individual task or reminder
- few perons as in a message, a lunch, an interview or a seminar
- numerous persons as in a broadcast message, a big party or a webinar
- belongs to a segment of your life
- Profesional
- Private
- Familial
- Social
- can be chained with other events
with roles
An event gathers one or many persons around a subject with specific roles. When you invite them you give them roles
- either you are the organizer (creator, owner, sender, responsible of this event)
- or you are an invitee (co-organizer, receiver, destinatory…)
- or just informed with no action
From invitee to participant
When you accept the invitation, you participate actively to the events with contributions, discussion, comments, votes and accelerate decision and business processes
In an event you have a role to play.
with life cycles
In gentle talk a chat can be instant and active at once, Structured events might need preparation and debrief
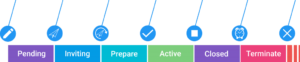
Before the event to be active you might want to prepare it, with as many steps as needed
- Pending: draft a document and a list of destinatory, make it approved
- Invite and send it, receive response and manage the invitees
- Prepare the needed logistics according to the number of participants
During at scheduled date time, you declare the event active and run the event, let you invitee collaborate with contributions, multi media document, comments and appreciations (like, rating, vote)
After the event, you may want to
- debrief
- close the event in sending the outcomes: minutes, and assign tasks, get the comments on the outcomes
- terminate and archive the event

of all participants
- your corporate/personal information
- those that are entrust to you
based on a mutual use of ChatCal:
I protect your information and you protect mine
An active security during event life
The event responsible (owner and co-owner) assure an active security during the event life.
They can manage:
- participants, in changing their roles and eventually ban an indelicate
- content and comments, in moderating the contributions, stop inappropriate content (even if they can’t delete it)
Proactive security in templates
Combining lifecycles and roles provides a proactive security. At each life cycle, the owner can change the role of each persons that can be saved in a template. For instance you might not want an invitee to contribute before the event to be “active”
Mobile rights policy
When information becomes mobile in smartphone and tablets, ChatCal protect their privacy with advanced “mobile rights“
Keep your devices “In-Sync”
A person can have many devices: Smartphone, tablet, laptop and desktop PC’s and choose the various devices that will participate in the event.
Each event and updates synchronize automatically, silently and securely in the “participating devices” of the participants, thus keeping your devices “in-Sync”.
This feature permits the multi device use: the participants can contribute many devices at the same time, consequently using the best suitable device:
- taking a picture is easier with a smartphone
- typing text is easier with a table or a PC.
The synchronization happens either on WIFI or telecom networks 3G, 4G, 5G using many security techniques
BlueSafe, the Record Management
At the end of an events, its content is automatically
- safely archived in BlueSafe, the record management in the Blue Digital safe
- and securely removed from all participating devices, the best mobile protection isn’it that the information does not reside in the mobile
- its information remains accessible to all participants according to their role